This flaw affected users of these devices: iPhone XS and later, iPad Pro 12.9-inch 2nd generation and later, iPad Pro 10.5-inch, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 6th generation and later, and iPad mini 5th generation and later. Someone with one of the aforementioned devices tapping on a malicious image could have given an attacker the opportunity to run any commands or codes on the target device. The update, once installed, removes this vulnerability from the affected devices.
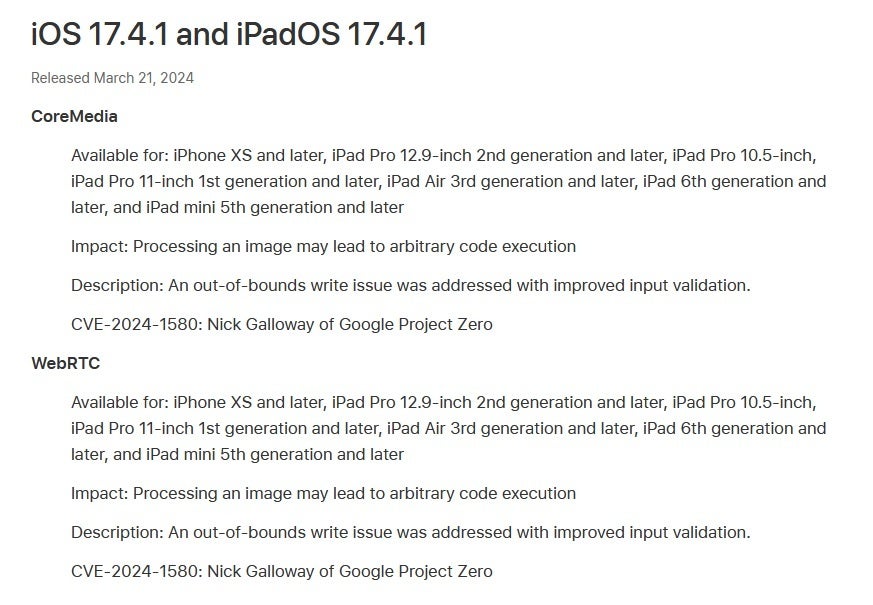

Apple updates its Security Releases support page to reveal the flaws fixed by iOS 17.4.1 and iPadOS 17.4.1
Apple didn’t say that it had any indication that the vulnerability was exploited. The simple description given by Apple read like this: “An out-of-bounds write issue was addressed with improved input validation.” Given the CVE-2024-1580 listing number, the flaw was discovered by Google Project Zero’s Nick Galloway.
The second vulnerability was a flaw in the system Apple calls WebRTC which provides “web browsers and mobile applications with real-time communication via application programming interfaces.” This flaw also impacted the same devices which we will gladly repeat: iPhone XS and later, iPad Pro 12.9-inch 2nd generation and later, iPad Pro 10.5-inch, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 6th generation and later, and iPad mini 5th generation and later.
This vulnerability, also not exploited by any attackers as far as Apple could tell, also would have allowed an attacker to run any commands or codes on a targeted device. The flaw was assigned CVE number CVE-2024-1580 and was also discovered by Nick Galloway of Google Project Zero
If you haven’t installed iOS 17.4.1 yet, go to Settings > General > Software Update and follow the directions.
#Apple #finally #reveals #security #issues #patched #iOS #17.4.1


